
In today’s hyper-connected world, critical system protection is no longer a luxury—it’s a necessity. From healthcare institutions and manufacturing plants to financial systems and national infrastructure, organizations rely on sensitive, high-availability systems to operate securely and efficiently. The failure or compromise of these systems can result in massive data loss, financial damage, legal penalties, and even risk to human life.
At its core, critical system protection refers to the methodologies, tools, and frameworks used to secure vital IT and operational systems from cyber threats, misconfigurations, and unauthorized changes. These protections apply not only to traditional information systems (like enterprise servers and databases) but also to industrial control systems (ICS), operational technology (OT) environments, and safety-critical systems in sectors like healthcare, energy, and transportation.
Why Is Critical System Protection Important Now?
The threat landscape is evolving, with cybercriminals increasingly targeting foundational systems. High-profile cyberattacks on pipelines, hospitals, and electrical grids have highlighted just how vulnerable critical infrastructure can be:
- The Colonial Pipeline attack (2021) led to gasoline shortages across the Eastern U.S.
- Ransomware incidents in hospitals disrupted patient care and endangered lives.
- State-sponsored attacks on water treatment facilities threatened public health.
A 2023 report by Cybersecurity Ventures estimates that cybercrime will cost the world $10.5 trillion annually by 2025, and much of that damage will stem from attacks on critical systems.
As a result, governments and industries are pushing for stronger protections, often mandating compliance with standards such as NIST Cybersecurity Framework, IEC 62443, and ISO/IEC 27001.
What You’ll Learn in This Guide
This in-depth guide explores every facet of critical system protection, including:
- What it is and how it differs from traditional cybersecurity
- Why it’s vital for both IT and OT environments
- The components of a strong protection strategy
- Frameworks and compliance standards
- Common tools and best practices
- How to implement a protection strategy
- Future trends and evolving threats
By the end, you’ll be equipped with a clear understanding of how to safeguard your most important systems—whether you’re a security professional, IT leader, compliance officer, or industrial engineer.
Quick Fact Table: Why Critical System Protection Matters
| Statistic / Case Study | Impact |
|---|---|
| Colonial Pipeline Ransomware (2021) | Shutdown of fuel supply to Eastern U.S., $4.4M ransom paid |
| 60% of OT environments experienced breach in 2023 | According to Palo Alto Networks’ Unit 42 report |
| Average downtime after critical system breach | 23 days (IBM Cost of a Data Breach 2023 Report) |
| 85% of companies lack mature ICS/OT security strategy | Source: SANS Institute ICS Survey |
2. What Is Critical System Protection?
Critical system protection refers to the implementation of specialized security strategies, tools, and processes designed to safeguard the most essential systems within an organization or infrastructure. These systems are considered mission-critical, meaning their failure or compromise would result in severe operational disruption, legal consequences, safety threats, or financial loss.
This type of protection goes beyond traditional cybersecurity by focusing on systems that must remain operational under all conditions, such as:
- Industrial Control Systems (ICS)
- Supervisory Control and Data Acquisition (SCADA) systems
- Safety Instrumented Systems (SIS)
- Healthcare devices and medical records systems
- Financial clearinghouses and data centers
- Energy and utility infrastructure
Unlike general cybersecurity, which aims to protect all digital assets, critical system protection prioritizes the security of systems that cannot afford downtime, even for routine maintenance.
Key Characteristics of Critical System Protection:
- Prevention-focused: Uses behavior-based controls to block threats before they execute.
- Policy-driven: Implements strict rules for system behavior, file access, and application execution.
- Lightweight agents: Designed to operate in resource-constrained environments.
- Applicable across IT and OT: Secures both digital and physical infrastructure components.
How Is Critical System Protection Different from Traditional Cybersecurity?
| Aspect | Traditional Cybersecurity | Critical System Protection |
|---|---|---|
| Focus | General IT assets | Mission-critical systems (e.g., ICS, OT, SCADA) |
| Tolerance for downtime | Some downtime acceptable | Zero tolerance for downtime |
| Strategy | Detection and response | Prevention and hardening |
| Example tools | Antivirus, EDR, SIEM | SCSP, behavior-based HIPS, air-gapped firewalls |
| Target sectors | All industries | Healthcare, energy, manufacturing, national infrastructure |
Case Study Example:
A North American utility company implemented Symantec Critical System Protection (SCSP) to protect its SCADA systems. The result was a 65% decrease in system configuration errors and zero reported malware intrusions for over 18 months.
3. Why Critical System Protection Matters: Real-World Importance
In an increasingly digitized world, the stability and reliability of critical systems are directly tied to national security, public safety, economic performance, and human life. Unlike general IT systems that can tolerate brief periods of downtime or compromise, critical systems cannot afford failure—not even for a moment.
Organizations that operate critical infrastructure are under constant pressure from:
- Cyber threats (ransomware, nation-state actors, insider risks)
- Regulatory bodies
- The need for 24/7 uptime
- Safety assurance protocols
These systems operate airports, power grids, water treatment facilities, hospitals, and defense systems, making them prime targets for malicious activity.
Notable Real-World Attacks on Critical Systems
| Incident | Description | Impact |
|---|---|---|
| Colonial Pipeline (2021) | Ransomware attack shut down one of the largest fuel pipelines in the U.S. | Fuel shortages, $4.4 million paid in ransom, massive public disruption. |
| Oldsmar Water Treatment Hack (2021) | Hacker tried to poison Florida’s water supply by increasing sodium hydroxide levels. | Stopped in time, but revealed vulnerabilities in public utilities. |
| U.K. NHS WannaCry Attack (2017) | Ransomware crippled hospital IT systems, delaying surgeries and patient care. | Estimated losses of £92 million, thousands of appointments cancelled. |
| Ukrainian Power Grid Attack (2015) | Advanced persistent threat (APT) actors shut down power to 230,000 residents. | First known successful cyberattack on a power grid. |
These events prove that threat actors are increasingly targeting operational technology (OT) and critical infrastructure, where the potential damage extends far beyond monetary loss.
Critical System Protection in Different Sectors
1. Healthcare Systems
- Protects patient data, connected medical devices, and hospital infrastructure.
- Prevents breaches that can compromise lives and violate HIPAA regulations.
2. Energy and Utilities
- Ensures operational continuity in power plants, nuclear stations, and smart grids.
- Meets requirements under NERC CIP and IEC 62443 frameworks.
3. Industrial and Manufacturing Environments
- Protects Programmable Logic Controllers (PLCs) and Human-Machine Interfaces (HMIs).
- Supports secure communication between systems in OT networks.
4. Financial Institutions
- Prevents tampering with real-time transaction systems and clearinghouses.
- Reduces risk of catastrophic service interruptions or compliance penalties.
5. Transportation and Aviation
- Guards critical air traffic control systems, public transit controls, and smart logistics platforms.
- Supports compliance with Department of Transportation (DoT) and FAA cybersecurity guidelines.

Expert Insight
“The attack surface of critical infrastructure has never been broader. With increasing digital transformation in OT, organizations need protection strategies that assume compromise and enforce security at the system level.”
— Nicole Perlroth, Author of “This Is How They Tell Me the World Ends”
How Critical System Protection Reduces Business Risk
Benefits of Implementing Critical System Protection:
- Reduced Downtime: Policies and host-based controls prevent zero-day exploits.
- Improved Compliance: Meets global and industry-specific regulatory mandates.
- Operational Continuity: Prevents system compromise that could halt core operations.
- Threat Isolation: Advanced behavioral controls reduce lateral movement of threats.
- Safety Assurance: Ensures that systems responsible for life and safety maintain functional integrity.
4. Key Components of Critical System Protection
Implementing effective critical system protection requires more than just firewalls and antivirus software. It demands a layered, proactive approach that integrates multiple security mechanisms to protect essential systems from both internal and external threats.
Each component plays a role in reducing attack surfaces, enforcing secure behavior, and maintaining system integrity and availability. Below are the core elements every critical system protection strategy should include.
4.1 Host-Based Intrusion Prevention and Detection Systems (HIPS/HIDS)
HIPS and HIDS are foundational technologies in endpoint security, especially for critical systems. These tools monitor and control host-level behavior, such as unauthorized file modifications, registry changes, and anomalous process behavior.
- Host-Based Intrusion Prevention Systems (HIPS) proactively block known or suspicious actions before they execute.
- Host-Based Intrusion Detection Systems (HIDS) analyze activity logs and generate alerts when potential breaches are detected.
Example: Symantec Critical System Protection (SCSP) provides behavior-based HIPS functionality designed for both physical and virtual environments. It uses granular policy enforcement and system hardening to mitigate zero-day vulnerabilities and unpatched software.
4.2 Behavior-Based Security Policies
Instead of relying solely on threat signatures or patching, behavior-based policies define what is allowed rather than what is blocked. These policies:
- Restrict which applications and services can run.
- Limit access to specific directories or system resources.
- Prevent unauthorized changes to system configurations.
Behavior-based security is especially useful in OT environments, where patching may be risky or infeasible. According to CISA’s guide on ICS security, these policies play a vital role in protecting unpatchable legacy systems.
4.3 Network and Perimeter Protection
Although critical system protection emphasizes host-level security, network defense remains essential for perimeter hardening and traffic monitoring.
Key tools include:
- Firewalls with application-layer filtering
- Intrusion Detection/Prevention Systems (IDS/IPS)
- Microsegmentation for isolating systems within internal networks
- VPN and encrypted channels for secure remote access
Source: The National Institute of Standards and Technology (NIST) recommends implementing network segmentation to isolate operational technology (OT) systems from external threats and administrative IT environments.
4.4 Safety Instrumented Systems (SIS) and Fail-Safe Controls
In industries such as oil and gas, manufacturing, and aviation, safety instrumented systems (SIS) are responsible for automatically shutting down operations in unsafe conditions. Protecting these systems is crucial to avoiding:
- Physical harm
- Environmental disasters
- Regulatory violations
Critical system protection tools should monitor and enforce secure behavior in these systems, including:
- Validating firmware integrity
- Logging communication between PLCs and sensors
- Monitoring for unauthorized configuration changes
For more technical depth, see ISA/IEC 61511: Functional Safety – SIS and how it supports secure fail-safe system design.
4.5 Compliance Frameworks and Industry Standards
Compliance is not just a checkbox—it provides a blueprint for building and maintaining resilient systems. A strong critical system protection strategy aligns with major regulatory frameworks, such as:
| Framework | Focus Area | Applies To |
|---|---|---|
| NIST CSF | Cybersecurity risk management | Government, private sector |
| IEC 62443 | ICS/OT cybersecurity | Manufacturing, energy, critical infrastructure |
| ISO/IEC 27001 | Information security management | Enterprises worldwide |
| NERC CIP | Electric grid reliability | Energy providers in North America |
| HIPAA Security Rule | Healthcare system security | U.S. healthcare industry |
These frameworks ensure that critical systems are:
- Properly inventoried
- Continuously monitored
- Regularly assessed for risk
- Secured by design
Real-World Application Example
Case Study: Healthcare Facility in Europe
A regional hospital used SCSP alongside behavior-based policies to protect its medical device infrastructure, including ventilators and imaging systems. After policy deployment:
- Unauthorized executable attempts dropped by 90%
- System patching downtime was reduced by 60%
- Regulatory compliance scores improved across 4 audits
This approach allowed the hospital to maintain patient safety, uptime, and data protection, all while satisfying EU GDPR and ISO/IEC 27001 guidelines.
5. How Critical System Protection Works: Step-by-Step Breakdown
Understanding how critical system protection functions in practice helps organizations implement the right measures in the right order. While tools and policies differ across industries and infrastructures, most effective strategies follow a similar operational lifecycle.
This section breaks down the critical system protection process into clear, manageable phases that align with both industry best practices and regulatory expectations.
Step 1: Asset Discovery and Classification
Before you can protect anything, you need to know what exists in your environment.
- Asset discovery identifies all critical endpoints, including servers, industrial controllers, legacy systems, IoT devices, and virtual machines.
- Asset classification groups those assets based on sensitivity, criticality, or compliance requirements.
Why this matters:
Unclassified or unknown assets are common entry points for attackers. According to the Ponemon Institute, over 60% of data breaches originate from unmanaged or unknown assets.
Tools used:
- Configuration Management Databases (CMDBs)
- Network scanning tools (e.g., Nmap, Rapid7, Nessus)
- Passive monitoring (e.g., Nozomi, Claroty for OT)
Step 2: Define Security Policies
Once assets are identified, security policies must be created to control behavior and limit exposure. These are not generic rules — they are tailored to the asset type, use case, and risk profile.
Policy types may include:
- Application whitelisting
- Registry and file system protection
- Memory and process monitoring
- Privilege control and escalation prevention
Example: In a financial data center, a policy might restrict access to SQL databases to only a subset of authenticated services running under specific conditions.
Step 3: Simulate and Audit Policies
Jumping straight into policy enforcement without testing can result in service outages or user friction.
- Simulation mode allows security teams to test policies in a real environment without actually enforcing them.
- Audit logs help teams refine policies by observing which processes would have been blocked or altered.
“Simulated enforcement gives security teams the freedom to adapt policy without disruption — which is critical in production environments.”
— Source: Symantec Data Center Security
Step 4: Policy Enforcement and Real-Time Protection
Once policies are refined, they are set to active enforcement mode.
This phase includes:
- Real-time blocking of unauthorized changes
- Event logging of violations
- Alerting and integrations with SIEM tools like Splunk, ArcSight, or QRadar
High-value targets like domain controllers, industrial PLCs, and medical devices are typically monitored continuously at this stage.
Step 5: Reporting, Compliance & Analytics
Organizations need to demonstrate security compliance to auditors, customers, or regulators. Reporting tools tied into the critical system protection solution deliver:
- Compliance dashboards (HIPAA, NIST, ISO, etc.)
- Change audit trails
- Threat trend analysis
These reports are essential for internal governance and external validation.
According to a report by ISACA, continuous monitoring through automated reporting boosts incident response times by up to 65%.
Step 6: Continuous Improvement and Adaptive Defense
Cybersecurity is not static. Threats evolve — and so should defenses.
- Regular policy reviews
- Threat intelligence updates
- Adaptive controls using machine learning
Security teams continuously tune protection mechanisms to align with:
- Emerging vulnerabilities
- New system deployments
- Changes in business priorities
Example: When the Log4j vulnerability was disclosed, many organizations updated their protection policies immediately to block exploitation attempts — even before formal patches were available.
Summary Table: The Critical System Protection Lifecycle
| Phase | Objective | Key Activities |
|---|---|---|
| Asset Discovery | Inventory critical systems | Scanning, passive mapping |
| Policy Design | Define behavior rules | Whitelisting, access control |
| Policy Simulation | Test policy without impact | Audit logging, dry-runs |
| Enforcement | Apply real-time controls | Blocking, alerting |
| Reporting | Prove compliance | Dashboards, logs |
| Improvement | Adapt to new threats | Policy tuning, intel updates |
6. Best Practices for Implementing Critical System Protection
Effective critical system protection is not just about deploying tools — it’s about implementing a well-planned, proactive, and constantly evolving strategy. Whether you’re a security analyst, IT administrator, or CISO, following industry-proven best practices can significantly improve the resilience of your systems.
This section outlines key best practices for deploying, maintaining, and optimizing critical system protection programs.
1. Start with a Comprehensive Risk Assessment
Begin by identifying what constitutes a critical system in your environment. These are typically:
- Systems with sensitive data (e.g., patient records, financial information)
- Infrastructure required for uptime (e.g., DNS servers, control systems)
- Legacy or unpatched systems (often vulnerable to exploits)
Conduct a formal risk assessment that maps:
- Assets to business functions
- Threat vectors to asset exposure
- Potential impact of compromise
Pro Tip: Use NIST’s Risk Management Framework (RMF) as a guideline for this step.
2. Apply the Principle of Least Privilege (PoLP)
Ensure that each user, application, or system process has only the permissions it needs — nothing more.
- Avoid giving admin access by default
- Use role-based access control (RBAC)
- Employ just-in-time (JIT) access for privileged tasks
“The principle of least privilege is a foundational control in reducing attack surfaces.”
— SANS Institute
3. Create and Enforce Tight Security Policies
Design detailed security policies based on:
- File system access
- Registry editing
- Application behavior
- Network connections
These policies should be enforced at the system level to block:
- Unauthorized scripts
- Unapproved binaries
- Known malicious behaviors
Tools like Symantec CSP, CrowdStrike Falcon, or Microsoft Defender for Endpoint provide policy-driven protection at the kernel level.
4. Implement Real-Time Monitoring and Alerting
Deploy real-time monitoring agents that log:
- System changes
- Network anomalies
- Unauthorized access attempts
Integrate with SIEM systems for unified visibility and rapid incident response. Use tools such as:
- Splunk
- IBM QRadar
- Elastic Security (formerly ELK)
5. Update and Patch Systems Frequently
Patching is one of the most basic yet often neglected areas in critical system protection.
Best practices:
- Maintain a patch management schedule
- Test patches in a controlled environment before production rollout
- Apply virtual patching in case of critical zero-day vulnerabilities
Case Example:
During the WannaCry ransomware outbreak, unpatched Windows systems were the entry point. Organizations that had updated systems avoided compromise.
6. Train Staff on Security Hygiene
Human error remains one of the top causes of cyber breaches. Regular training should include:
- Recognizing phishing attempts
- Password management
- Physical access protocols
- Incident reporting procedures
Provide quarterly refreshers and simulate attack scenarios using tools like KnowBe4 or Cofense.
7. Continuously Review and Refine Security Posture
Cyber threats evolve — and so must your protection.
Establish a continuous improvement loop:
- Monitor threat trends
- Reassess policies quarterly
- Update systems and rulesets
- Simulate attacks (e.g., red teaming, pen testing)
This approach aligns with frameworks such as MITRE ATT&CK and ISO/IEC 27001.
Best Practices Summary Table
| Best Practice | Why It Matters | Tools / Frameworks |
|---|---|---|
| Risk Assessment | Identify critical systems & threats | NIST RMF, ISO 27005 |
| Least Privilege | Limit attack surface | RBAC, PoLP |
| Security Policies | Define safe system behavior | Symantec CSP, Microsoft Defender |
| Real-Time Monitoring | Detect issues instantly | Splunk, QRadar, Elastic |
| Patch Management | Prevent known exploits | SCCM, WSUS, Qualys |
| Staff Training | Reduce human error | KnowBe4, Cofense |
| Continuous Review | Adapt to new threats | MITRE ATT&CK, Red Team Ops |
Expert Insight
“No matter how advanced your tools are, your security posture is only as strong as your weakest process.”
— Dr. Eric Cole, Cybersecurity Expert & Former CIA Analyst7. Top Critical System Protection Tools (Comparison & Features)
Choosing the right critical system protection tools can make or break your organization’s ability to detect, prevent, and respond to advanced threats. While policies and practices form the foundation, tools enable enforcement, automation, and intelligence-driven decision-making.
This section provides a detailed comparison of the most effective tools currently used to protect critical infrastructure and high-value systems across IT and OT environments.
Leading Critical System Protection Tools
Tool Name Primary Use Case Key Features Ideal For Symantec Critical System Protection (CSP) System hardening, real-time monitoring Host-based intrusion prevention (HIPS), granular policy enforcement, tamper protection Enterprises with complex endpoint ecosystems CrowdStrike Falcon Endpoint detection and response (EDR) Cloud-native EDR, threat hunting, machine learning analytics Mid to large enterprises Microsoft Defender for Endpoint Unified endpoint security Threat analytics, automated investigation, integration with Azure security stack Organizations in the Microsoft ecosystem Trend Micro Deep Security Virtual patching, application control Network-based and agent-based protection, anti-malware, firewall Hybrid cloud and virtualized environments Carbon Black (VMware) Behavioral analytics, threat prevention Lightweight agent, continuous recording, application control Organizations with compliance-heavy mandates McAfee Application Control Whitelisting and change control Dynamic application whitelisting, integrity control, change management Industrial systems, POS, and embedded devices
Tool Feature Deep Dive
1. Symantec CSP
- Use Case: Harden systems by restricting unwanted behavior at the kernel level.
- Strengths: Excellent for legacy systems and environments requiring zero trust enforcement.
- Limitation: Requires significant upfront policy configuration.
2. CrowdStrike Falcon
- Use Case: Advanced threat detection using behavioral analytics.
- Strengths: Fast deployment, strong cloud-native architecture.
- Limitation: May be excessive for smaller organizations.
3. Microsoft Defender for Endpoint
- Use Case: Integrated protection for Windows-heavy environments.
- Strengths: Seamless integration with Active Directory, Office 365, and Azure Sentinel.
- Limitation: Limited visibility into non-Windows environments.
4. Trend Micro Deep Security
- Use Case: Ideal for dynamic data centers and hybrid cloud.
- Strengths: Deep integration with AWS, Azure, and VMware.
- Limitation: Licensing may be complex for smaller businesses.
5. Carbon Black
- Use Case: Compliance-driven behavioral protection.
- Strengths: Continuous endpoint visibility and rollback capabilities.
- Limitation: Requires tuning to reduce false positives.
6. McAfee Application Control
- Use Case: Secure fixed-function systems.
- Strengths: Strong protection for industrial systems and critical machines.
- Limitation: Can be rigid in rapidly changing software environments.
Key Considerations for Selecting a Tool
When choosing a critical system protection solution, consider the following:
- System Type: Are you protecting traditional endpoints, OT/ICS systems, or cloud-native workloads?
- Compliance Requirements: Do you need to meet standards like NERC CIP, ISO/IEC 27001, HIPAA, or GDPR?
- Operational Overhead: Can your team manage the tool’s configuration, updates, and alerting?
- Integration Needs: Does the tool support your existing tech stack (e.g., SIEM, SOAR, EDR)?
- Scalability: Can it grow with your organization?
Security Framework Mapping
Security Framework Suggested Tools NIST Cybersecurity Framework (CSF) Symantec CSP, CrowdStrike, Microsoft Defender MITRE ATT&CK CrowdStrike Falcon, Carbon Black, Trend Micro ISO/IEC 27001 Microsoft Defender, McAfee App Control, Trend Micro IEC 62443 (Industrial) McAfee Application Control, Symantec CSP
8. Compliance and Regulatory Requirements for Critical System Protection
For organizations that operate in regulated industries—such as healthcare, finance, energy, or critical infrastructure—compliance is not just a best practice, it’s a legal mandate. Proper implementation of critical system protection strategies must align with industry-specific regulatory frameworks and cybersecurity standards to avoid legal penalties, data breaches, and reputational harm.
Why Compliance Matters in Critical System Protection
Regulatory bodies around the world have established frameworks that dictate how sensitive systems and data should be secured. Failing to adhere to these regulations can lead to:
- Financial penalties in the millions of dollars
- Loss of licenses or operating privileges
- Increased scrutiny from regulators
- Irreparable brand damage
Cybercriminals often exploit the weakest systems—especially those that lack enforced compliance controls. Adherence to cybersecurity standards reduces vulnerabilities, ensures accountability, and builds trust with customers and stakeholders.
Major Regulatory and Security Standards
Below is an overview of key standards that influence critical system protection across industries:
| Framework / Standard | Applicable Sectors | Focus Areas |
|---|---|---|
| NIST Cybersecurity Framework | Federal agencies, private sector (USA) | Identify, Protect, Detect, Respond, Recover |
| ISO/IEC 27001 | Global, all sectors | Information Security Management System (ISMS) |
| NERC CIP | Energy and utility companies (North America) | Critical infrastructure protection in power grids |
| HIPAA | Healthcare (USA) | Electronic health data privacy and security |
| PCI-DSS | Payment and financial sectors | Protection of cardholder data and transaction environments |
| GDPR | Businesses handling EU citizen data | Data protection, consent, and breach reporting |
| IEC 62443 | Industrial and operational technology (OT) | Cybersecurity for industrial control systems |
How These Standards Relate to Critical System Protection
- NIST CSF provides a high-level, flexible approach that helps organizations structure their cybersecurity risk management and protection practices. It’s widely adopted in both public and private sectors.
- ISO/IEC 27001 requires organizations to implement controls (Annex A) that cover everything from asset management and access control to system acquisition and cryptographic protection—core elements of critical system protection.
- NERC CIP mandates specific measures to protect Bulk Electric Systems (BES), including physical and logical access control, incident response, and personnel training.
- HIPAA mandates administrative, physical, and technical safeguards for healthcare systems, ensuring that critical patient data and systems are protected against unauthorized access.
- IEC 62443 specifically addresses the needs of ICS and OT environments, where traditional IT protections fall short. It defines roles and responsibilities for system integrators, asset owners, and product suppliers.
Best Practices for Ensuring Compliance in Critical System Protection
To effectively meet compliance mandates, organizations should implement the following best practices:
- Conduct regular audits and risk assessments
- Document security policies and procedures
- Implement least-privilege access controls
- Use role-based security profiles and identity management
- Encrypt data in transit and at rest
- Maintain detailed event logging and system monitoring
- Create an incident response plan aligned with regulatory expectations
- Train employees regularly on compliance and security protocols
Compliance Pitfalls to Avoid
Even well-intentioned organizations can fall short. Common issues include:
- Relying solely on checklists without deeper risk analysis
- Failing to update systems in response to evolving regulations
- Ignoring OT-specific needs in industrial compliance strategies
- Underestimating the need for employee training
9. How to Implement a Critical System Protection Strategy (Step-by-Step Guide)
Establishing a robust critical system protection strategy requires careful planning, coordination, and execution across all levels of your organization. This section breaks down the process into actionable steps that align with both technical and organizational needs.
Step 1: Identify and Classify Critical Systems
Start by conducting a comprehensive asset inventory to determine which systems are critical. These typically include:
- SCADA systems
- Industrial control systems (ICS)
- Enterprise resource planning (ERP) systems
- Customer databases
- Cloud-based workloads
- Network infrastructure
Once identified, classify them by risk, sensitivity, and business impact. Use a framework like NIST SP 800-53 or ISO 27005 to guide this process.
“You can’t protect what you don’t know exists.” – Common axiom in cybersecurity
Step 2: Perform a Threat and Vulnerability Assessment
Assess your systems for vulnerabilities using automated tools and manual methods. This step involves:
- Vulnerability scanning
- Penetration testing
- Threat modeling
- Configuration audits
Use threat intelligence feeds (like MITRE ATT&CK) to stay updated on evolving tactics used against critical infrastructure.
Step 3: Define Security Policies and Governance
Security policies provide the foundation for critical system protection. Develop documentation that includes:
- Acceptable use policies
- Access control policies
- Change management procedures
- Incident response protocols
- Backup and disaster recovery strategies
Ensure these policies are approved at the executive level and enforced throughout the organization.
Step 4: Implement Technical Security Controls
Now, apply security controls that enforce the policies. These include:
| Control | Purpose |
|---|---|
| Firewalls and segmentation | Isolate critical systems from less secure areas |
| Multi-factor authentication (MFA) | Strengthen identity verification |
| Endpoint protection | Defend against malware, exploits, and ransomware |
| Data encryption | Protect data at rest and in transit |
| Logging and monitoring | Detect unauthorized access or anomalies |
Tools like CrowdStrike, Palo Alto Networks, and Tripwire Enterprise are commonly used to monitor and protect critical systems.
Step 5: Conduct Employee Training and Awareness
Humans remain one of the largest attack vectors. Provide regular cybersecurity training that includes:
- Social engineering and phishing prevention
- How to handle sensitive data
- What to do in case of a suspected breach
- Role-specific responsibilities in system protection
Training should be ongoing and updated as new threats emerge.
Step 6: Establish Incident Response and Recovery Plans
Prepare for the worst by developing a detailed incident response plan. This should include:
- A dedicated incident response team (IRT)
- Clear communication channels
- Isolation procedures for compromised systems
- Integration with law enforcement (if required)
Also, implement and test disaster recovery and business continuity plans to ensure critical operations can resume quickly.
Step 7: Continuously Monitor and Improve
Critical system protection is not a one-time setup. Continuously monitor systems and:
- Conduct regular risk assessments
- Patch known vulnerabilities
- Review and revise security policies
- Audit logs and respond to anomalies
- Simulate attack scenarios (e.g., red teaming)
Adopt a DevSecOps approach where security is integrated into every stage of system development and operations.
Step 8: Leverage Automation and AI for Protection
Modern security solutions use machine learning and AI to identify threats faster than human analysts. Consider:
- AI-based anomaly detection (e.g., Darktrace)
- Automated compliance reporting (e.g., Drata)
- SOAR platforms (Security Orchestration, Automation, and Response) to speed up remediation
Automation helps reduce human error and scale your protection efforts efficiently.
10. Real-World Case Studies in Critical System Protection
Studying real-world examples of critical system protection offers valuable insights into the challenges, strategies, and technologies used by organizations to defend vital infrastructure. Below are several notable case studies across industries, demonstrating how critical system protection is implemented under pressure.
Case Study 1: Colonial Pipeline Ransomware Attack (2021)
Industry: Energy & Infrastructure
Threat: Ransomware attack via compromised VPN credentials
Outcome: Fuel shortages across the U.S. East Coast, $4.4 million ransom paid
Protection Lessons:
- Zero Trust Architecture: The attacker gained access through an unused VPN account. A zero trust model would have required continuous verification and denied access based on abnormal behavior.
- Segmentation: The attack shut down IT systems, prompting the company to also halt OT systems. Strong segmentation could have allowed the OT systems to remain operational.
- Incident Response Readiness: The breach highlighted the importance of having well-rehearsed incident response plans, which were lacking at the time.
“This attack underscores the vulnerability of our infrastructure and the urgency of critical system protection.” – U.S. Department of Homeland Security
Case Study 2: Maersk – NotPetya Attack (2017)
Industry: Global Shipping & Logistics
Threat: State-sponsored malware, disguised as ransomware
Outcome: Estimated $300 million in losses, 49,000 infected endpoints
Protection Lessons:
- Backup and Recovery: The company recovered by relying on a single surviving domain controller located in Ghana. This proves the necessity of geographically diverse, offline backups.
- Patch Management: The malware exploited an unpatched Windows vulnerability (EternalBlue). Regular patching schedules could have prevented the exploit.
Maersk’s recovery took over 10 days, during which shipping operations were crippled. Today, they’ve implemented a resilient cybersecurity architecture, making them a case study in security transformation.
Case Study 3: Target POS Breach (2013)
Industry: Retail
Threat: Malware infiltration through HVAC vendor
Outcome: 40 million credit card numbers stolen, $162 million loss
Protection Lessons:
- Vendor Access Control: The attacker gained entry through a third-party vendor. Strong third-party risk management and network segmentation could have prevented lateral movement.
- Enhanced Monitoring: Security tools did detect the anomaly, but alerts were ignored. This stresses the importance of security information and event management (SIEM) tools with actionable alerting.
“Critical system protection must include supply chain and third-party partners as part of your security perimeter.” – SANS Institute
Case Study 4: Stuxnet Worm Attack on Iranian Nuclear Program
Industry: Nuclear Infrastructure
Threat: Nation-state-developed worm targeting ICS/SCADA systems
Outcome: Physical destruction of uranium centrifuges
Protection Lessons:
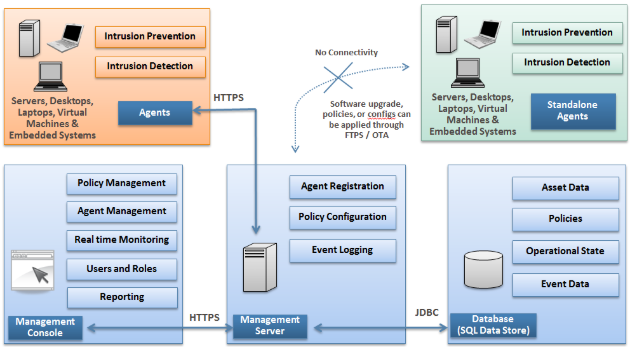
- Air-Gapped Networks Are Not Immune: Stuxnet was delivered via USB, bypassing air gaps. Relying solely on isolation is inadequate.
- Behavioral Detection: Traditional antivirus solutions failed. Advanced behavioral analytics and whitelisting would have provided better protection.
- OT-Specific Security Tools: This attack highlights the need for ICS-aware security tools, which understand OT protocols like Modbus and DNP3.
Stuxnet remains one of the most sophisticated cyberattacks ever discovered and fundamentally changed how we approach industrial system protection.
Common Themes Across All Case Studies
| Security Element | Observations |
|---|---|
| Asset Visibility | Most victims lacked a clear inventory of systems or external connections |
| Patch Management | Delays in patching known vulnerabilities led to successful exploits |
| Vendor & Third-Party Access | Weak controls allowed attackers to infiltrate through indirect channels |
| Monitoring & Alerting | Alerts existed but were not acted upon due to alert fatigue or poor configuration |
| Backup and Recovery | Effective only when tested regularly and stored securely |
Conclusion from Case Studies
Each case reinforces the importance of a multi-layered defense strategy, tailored to your specific threat landscape and regulatory requirements. These real-life scenarios also show that critical system protection is not a one-size-fits-all process—it must evolve with your infrastructure, the threat environment, and technological advances.
